Web Application Penetration Testing Methodology: Ensuring Online Security

Introduction
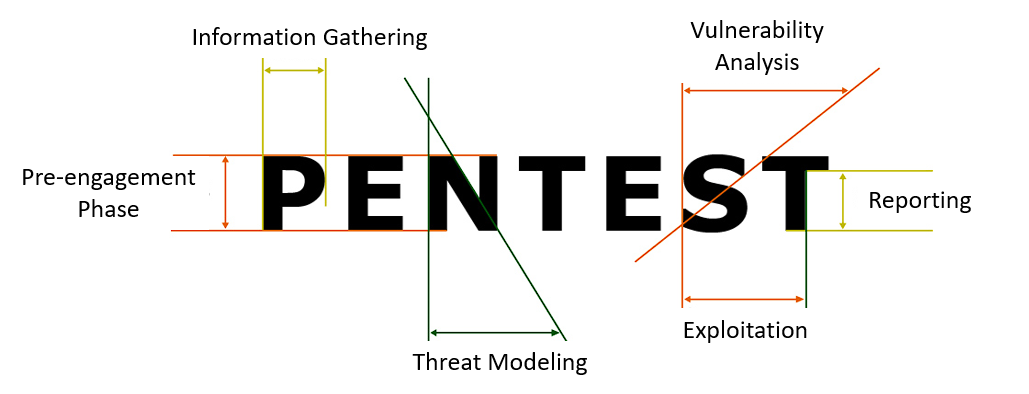
Pre-engagement Phase
Key tasks during this phase include — a. Define Scope — Identify the target application, its subdomains, and specific functionalities to be tested. Determine any restrictions, such as no data alteration or denial-of-service testing. b. Obtain Permissions — Seek proper authorization from the application owner or responsible parties to conduct the penetration testing exercise. c. Agreement and Legalities — Document the terms of engagement, including confidentiality clauses and limitations, in a formal agreement.
Information Gathering
In this phase, the penetration tester collects as much information as possible about the target web application. Various tools and techniques are used to extract valuable data, such as —
- Passive Reconnaissance — Use search engines, social media, and publicly available sources to gather information about the organization, employees, and potential security loopholes.
- Active Reconnaissance — Employ network scanning tools like Nmap or automated web crawlers to identify the application’s structure, ports, and services.
Threat Modeling
Vulnerability Analysis

Common vulnerabilities to look for include —
- Injection Attacks — Check for SQL injection, NoSQL injection, and other code injection vulnerabilities.
- Cross-Site Scripting (XSS) — Verify if the application is susceptible to reflected or stored XSS attacks.
- Cross-Site Request Forgery (CSRF) — Test for CSRF vulnerabilities that could lead to unauthorized actions on behalf of users.
- Authentication and Authorization Issues — Evaluate the strength of password policies, session management, and access controls.
- Insecure Direct Object References (IDOR) — Assess if sensitive resources are adequately protected from unauthorized access.
- Security Misconfigurations — Look for default credentials, unnecessary services, and other misconfigurations.
- File Upload Vulnerabilities — Check for inadequate validation and filtering on uploaded files.
Exploitation
Post-Exploitation
Reporting
After completing the testing process, the penetration tester compiles a comprehensive report detailing the findings.
The report should include —
- Executive Summary — A non-technical overview of the findings and their potential impact on the business.
- Technical Details — A detailed description of each vulnerability, including how it was discovered and exploited.
- Risk Level — An assessment of the severity and potential consequences of each vulnerability.
- Recommendations — Clear and actionable recommendations to address the identified vulnerabilities.
- Remediation Steps — Guidance on how to fix the vulnerabilities and improve the overall security posture.
- Acknowledgments — Recognizing the cooperation of the application owner and any involved parties.
Retesting
During retesting, the penetration tester focuses on the following tasks —
- Confirming Remediation — The tester validates whether the reported vulnerabilities have indeed been fixed. This involves attempting to exploit the vulnerabilities again and ensuring that they no longer pose a risk.
- Regression Testing — While fixing vulnerabilities, developers may inadvertently introduce new issues. The penetration tester should perform regression testing to ensure that the fixes did not create any new security problems.
- Reviewing the Fix — The tester examines the changes made by the development team to ensure they are robust and comprehensive, leaving no room for recurrence of the vulnerabilities.
- Assessing the Impact — In some cases, the fix may have an impact on other areas of the application or system. The tester assesses whether the changes have any adverse effects on the application’s functionality and performance.
Reporting (Post-Retesting)
After completing the retesting phase, the penetration tester compiles a new report that highlights the results of the retest.
The post-retesting report should include —
- Confirmation of Remediation — A clear statement indicating whether the previously reported vulnerabilities have been successfully remediated or not.
- New Findings (if any) — If any new vulnerabilities were discovered during the retesting phase or as a result of the fixes, they should be documented along with their severity and recommended remediation.
- Updated Risk Assessment — If vulnerabilities have been successfully remediated, the risk levels associated with the application should be updated accordingly.
- Additional Recommendations — Any additional recommendations or best practices that were identified during the retesting phase should be included.
- Final Approval — The report should be reviewed and approved by relevant stakeholders before it is considered finalized.
Conclusion
For more details find OWASP pentest methodologies Link